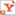Using OpenPGP with Evolution
Email is an everyday means for communication. The need to provide confidentiality and authenticity to conversations is there, and a growing number of users are starting to realize it. Hence this article which will hopefully guide you to start considering it yourself.
The reason my first article is about Evolution is that it was requested. Hopefully I’ll get time to write articles involving other mail clients as well.
If you don’t know the difference between S/MIME and OpenPGP, or want to know more about why you should digitally sign and encrypt emails, please read to our article A focus on secure communication: Why you should sign and encrypt your emails
About Evolution
Evolution1 is an integrated solution for email, contacts and calendar. It was originally developed by Novell but is now an Open Source project. It is first and foremost for the GNOME2 desktop system, but it work well for KDE3 as well, of which the screenshots of this article is based on.
Evolution include several features, including SpamAssassin4 for junk filtering. I’ll focus most on the feature they call "Security and encryption". Evolution include support for both S/MIME and OpenPGP, but the focus of this article will be around OpenPGP.
Using Evolution
Evolution use GNU Privacy Guard5 for its OpenPGP support. If you have this configured already it will start using Evolution with it straight away, as it automatically verifies signatures and decrypts messages. If you don’t have GnuPG configured, refer to our article on Setting up GnuPG and using it together with kgpg.
Verifying signatures
This is a message that has been digitally signed, but not encrypted. You can clearly see the “Valid signature” tag at the bottom of the emails.
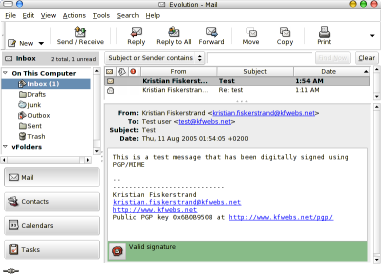
If you encrypt the email the window will look like:
Small drawback to Evolution
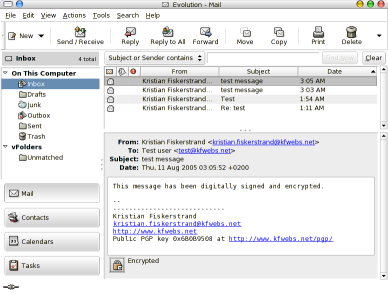
One thing I encoutered here is that Evolution (at least my version, version 2.2.3) require the encrypted data to be RFC 1847 Encapsulated. It does not support the other method of both digitally signing and encrypting as defined in RFC 3156. (RFC 1847 encapsulation is described in chapter 6.1, the combined method is described in chapter 6.2 for those interested).
My primary mail client, Mozilla Thunderbird, with Enigmail as an extension to handle the security use the combined method by default when sending a message using PGP/MIME. It will be able to properly verify both methods.
Verified and decrypted
A message that was sent with the signature encapsulated will show the following. This is the same as it should show for the previous message as well.
Signing and encrypting emails
Now, to signing and encrypting emails yourself you will have to tell Evolution to do so. By going to the security tab in the preferences you get
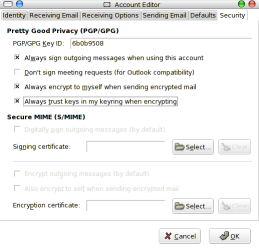
Once you have configured it, you have to tell Evolution to sign and encrypt the email of which you are about to send. You do this by checking PGP Sign and PGP Encrypt in the Security dropdown.
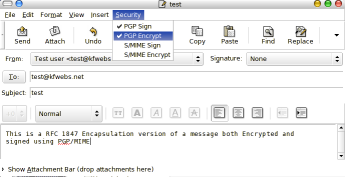
Requirements
Now, both signing and encryption of email messages require that the keyring has been configured beforehand. Evolution will sign using the key specified and try to encrypt messages using the email addresse to match with a user id in a PGP key.
As Evolution doesn’t in itself support key management, if you would like to learn more about key management, refer to our article on the subject of key management using kgpg. This might be found at http://www.kfwebs.net/articles/article/20/A+focus+on+secure+communication+kgpg. Another option is to just use the commandline
References
- http://www.gnome.org/projects/evolution/
- http://www.gnome.org/
- http://www.kde.org/
- http://www.spamassassin.org
- http://www.gnupg.org